DNS Proxywall
Technical Specifications
| Latest release |
5.67 ,
24 Jul 2024 ,
[Change Log, Previous Releases]
|
|
Supported networking
|
Ethernet, IPv4, IPv6, TCP, UDP, DNS. |
|
Traffic transformation engine
|
Kernel-mode network driver. |
| Prerequisites |
.NET 4.5.2, up-to-date root certificates (or it will take
2 minutes to start).
|
| Supported OSes |
Windows 7*, 8, 8.1, 10, 11, Server 2008 R2*, Server 2012, Server 2012 R2, Server 2016, Server 2019, Server 2022.
*For Windows 2008 R2 and 7, required Service Pack 1 +
KB3033929 (SHA-2 digital signing).
*For Windows 8.1, Server 2012 R2, required KB2995730.
|
| Recommended hardware |
CPU 1GHz and above, modern graphics card. |
| Additional hardware required |
none |
Overview
Domain Name System (DNS) is the way web browsers obtain IP
addresses of Internet servers.
DNS Proxywall uses flexible set or rules to restrict access to
websites by name patterns and geographical locations.
It can also act as a proxy that provides filtering and caching
of server names for other computers.
To better understand the options when choosing a DNS protection, please see
DNS firewall, DNS proxy, and DNS proxywall. Which
one to choose?
DNS Proxywall
DNS Proxywall is a perfect combination of DNS Firewall and DNS Proxy in one product. It has a
number of features that excites even the most demanding users:
- DNS cache - accelerates web browsing by resolving names instantaneously.
- Editing of DNS records - allows to specify your own IP addresses for DNS names.
- DNS monitoring - allows to see in real-time domain names being resolved as well as the countries of their location.
It also allows (on wired networks) to see which DNS names are resolved by other computers on the same network. The log can
be viewed and stored into a file for later analysis.
-
Activity view filters - allow to keep on screen only
important events (blocked, resolved via server, resolved via cache, etc.) for viewing.
They filter out the noise and bring only important events right at
user's eyes with a click of a button.
-
DNS performance measurement - allows to measure
round-trips of DNS packets during the name resolution to get an idea of how fast DNS names are being resolved. Multiple
performance metrics allow to make analytical decisions about the upstream DNS servers and about the currently connected
proxy clients.
-
DNS Proxy - allows other computers to connect in to use its cache or to use its DNS forwarding capabilities.
There are several modes of operation supported: standard DNS and DNS tunnel (when DNS traffic goes inside of the TCP traffic).
These modes can even work concurrently. DNS Proxy also supports TCP tunneling inside the encrypted SSL/TLS traffic.
-
Cascading of multiple DNS Proxywall servers - allows to organize them into a chain. Such a chain can consolidate
standard DNS traffic into a TCP tunnel on one end, forward to wherever is needed, then extract the standard DNS traffic
from it on the other end and forward it to any other standard DNS server. Juggle your DNS traffic whichever way you want.
-
Authentication - provides additional security between DNS Proxywall and DNS clients using self-signed certificates.
There is no need to pay for certificates, just generate a certificate (within the program) and provide its signature to
the other side. So the two sides of communication (DNS Proxy server and DNS Proxy client) can recognize each other. The
access to DNS Proxy capabilities can also be restricted by specifying the exact IP address and subnets of allowed DNS clients.
- Load balancing - allows to manually select the algorithm of forwarding DNS packets to multiple DNS servers.
- The internal IP Firewall - allows to block not resolved via DNS addresses. It adds a solid layer of security
that protects from malicious code that is trying to circumvent standard communication pathways.
- Geo tools - allow to quickly identify which country/territory server addresses belong to.
- And more, and more, and more...
DNS Monitoring
IMPORTANT: When used on a Virtual Machine, accidental changes by a user to the rules may affect Remote Desktop (RDP) traffic and result in a user lock out.
For instructions on how to restore RDP connectivity for a VM, see KB article Restoring Remote Desktop (RDP) connectivity to Azure VM after a user lock out.
DNS Proxywall offers extensive capabilities for DNS
traffic monitoring. It monitors the standard DNS traffic
between the local computer and remote DNS servers:
-
Outgoing DNS traffic originated on the local computer and
sent to remote DNS servers
-
Incoming and outgoing traffic between DNS clients and
DNS Proxywall
-
Incoming DNS traffic for local DNS server (if there is a
DNS server on the local computer)
- Promiscuous monitoring of traffic between other computers on the local wired network
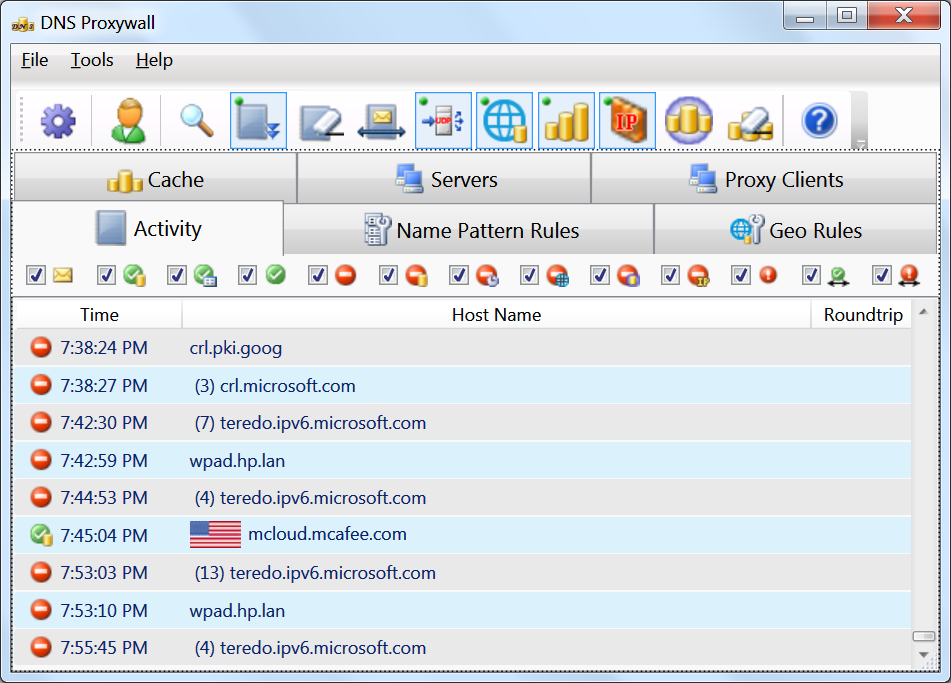
The activity log shows the status and the action that was taken on the traffic:
-
 - DNS query was sent the response was not yet received.
- DNS query was sent the response was not yet received.
-
 - DNS request was successfully resolved via local DNS cache.
- DNS request was successfully resolved via local DNS cache.
-
 - DNS request was successfully resolved via internal table of permanent host addresses.
- DNS request was successfully resolved via internal table of permanent host addresses.
-
 - DNS request was successfully resolved by DNS server.
- DNS request was successfully resolved by DNS server.
-
 - DNS request was blocked by name pattern rules.
- DNS request was blocked by name pattern rules.
-
 - DNS request was blocked due to cached response from DNS server contained name resolution refusal.
- DNS request was blocked due to cached response from DNS server contained name resolution refusal.
-
 - DNS request was blocked due to timeout (exceeded timeout threshold).
- DNS request was blocked due to timeout (exceeded timeout threshold).
-
 - DNS request was blocked due to geography.
- DNS request was blocked due to geography.
-
 - DNS request was blocked due to DNS cache only mode and the name was not in the cache.
- DNS request was blocked due to DNS cache only mode and the name was not in the cache.
-
 - non-DNS (direct address) connectivity was blocked by IP firewall since the IP address does not have matching record
within the cache.
- non-DNS (direct address) connectivity was blocked by IP firewall since the IP address does not have matching record
within the cache.
-
 - DNS request was refused by the server (the DNS server was unable to resolve the name).
- DNS request was refused by the server (the DNS server was unable to resolve the name).
-
 - DNS request was picked up in promiscuous monitoring mode and was resolved by DNS server for some other computer.
- DNS request was picked up in promiscuous monitoring mode and was resolved by DNS server for some other computer.
-
 - DNS request was picked up in promiscuous monitoring mode and indicates it the failure to resolve the name was communicated
between two other computers.
- DNS request was picked up in promiscuous monitoring mode and indicates it the failure to resolve the name was communicated
between two other computers.
Settings
Upstream DNS Servers
DNS Proxywall can forward packets to other DNS servers. Such DNS servers are
called 'upstream' servers since they are located up the stream.
The upstream DNS servers can be configured automatically by
the program or specified manually.
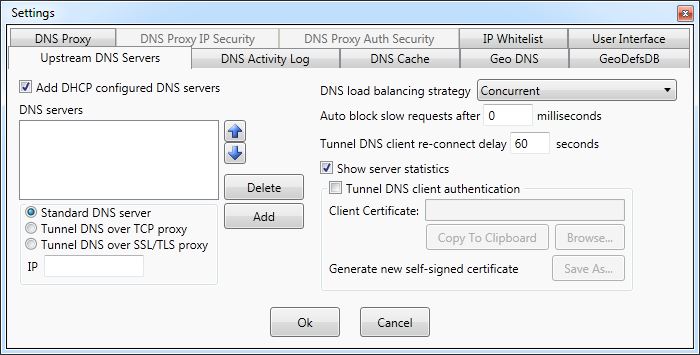
Add DHCP configured DNS servers option automatically
adds to the list standard DNS servers configured during
computer connect to the network (during DHCP configuration
phase).
DHCP configured servers are standard DNS servers that accept incoming
requests within DNS protocol over UDP. The upstream servers
can be also be added by manually specifying their IP
addresses. Only the following types of up-stream servers
are currently supported:
-
Standard DNS server - a regular server the most often used on the Internet for DNS resolution. Such servers use DNS
over UDP protocol.
-
Tunnel DNS over TCP proxy - a server uses a
proprietary DNS over TCP protocol which wraps DNS traffic into a single TCP tunnel connection to the upstream DNS
Proxywall.
-
Tunnel DNS over SSL/TLS proxy - a server uses a
proprietary protocol which wraps DNS traffic into a single TCP over SSL/TLS encrypted
tunnel to the upstream DNS Proxywall.
When forwarding to multiple upstream DNS servers,
DNS Proxywall uses load balancing strategy
which includes the algorithm for server selection.
Currently supported algorithms are:
- Local Only Unchanged -
- First Server Only - all requests are sent to only the first server on the list.
-
Round Robin - a request sent to the first server
on the list. The next request sent to the next server on the
list, and so on.
-
Round Robin on timeout - all request are sent to the first server on the list until its first timeout. Then, all
requests are sent to the next server on the list, and so on.
-
Concurrent - requests are sent to all DNS servers simultaneously.
The first received response is taken as a result.
Sometimes forwarded to upstream DNS
servers requests are taking to much time. The option Auto block slow requests allows to specify
the timeout when
to treat the lack of response as a response with refusal(rejection).
When an upstream connection is a tunnel to another DNS Proxywall, the connection is maintained
as a keep-alive connection. It does not break after each request.
If for any reason the connection breaks, DNS
Proxywall would attempt to re-connect after the specified delay. This
delay gives the network and the upstream DNS Proxywall some
time to resolve the issue.
All statistics on the number of blocked queries, the number of responses from cache and from remote servers
are displayed on the
Servers tab of the main window. The settings option Show server statistics enables that
Servers tab.
When an upstream connection is a TCP or SSL/TLS tunnel to another DNS Proxywall, authentication can be used to prevent unauthorized
access.
The verification of access is performed using certificates which
could be
standard certificates issued by certificate authorities or
self-signed certificates.
Tunnel DNS client authentication option enables such authentication.
Once authentication is enabled, the DNS Proxywall provides the same certificate to all upstream servers.
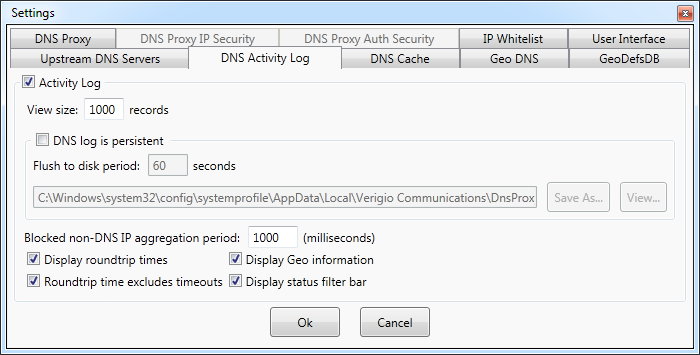
Settings - DNS activity log
Activity log shows all DNS related requests and responses.
View size setting specifies the number of records shown
within the user interface window. The default value is 1000.
User-interface is a performance demanding part of the application.
Therefore, the smaller values improve overall performance on servers and workstations with low-end graphics
cards.
The activity log can be persistent (stored into a file). This feature can be enabled with DNS log is persistent
checkbox. The persistent log is stored (flushed) to disk periodically with the interval specified in Flush to disk period.
Activity log files can grow to a very large size. For that reason, they are rotated every day. Each day is stored
within the same folder into a log file with a different suffix.
The location of the logs can be changed. The logs are
produced by the service component of the DNS Proxywall. Therefore they
keep growing even when user interface is not running.
The default location for the logs is
"C:\Windows\system32\config\systemprofile\AppData\Local\Verigio\DnsProxywallSvc\Logs\".
When DNS Proxywall blocks IP addresses, the number of blocked
packets could be astronomical. For that reason, the records with the same IP are aggregated and reported
as a single line.
The aggregation interval for IP blocking can be set in Blocked non-DNS IP aggregation period.
Other attributes related to resolved and blocked records can be added or removed from the view.
-
Display round-trip times - shows on the screen the time it took to resolve
a DNS record. It is the round-trip from this computer to the DNS server. It is not related to
round-trip to the actual
server destination stated within the DNS record.
-
Round-trip time excludes timeouts - excludes timed-out
requests (DNS server did not respond) from round-trip
calculation. When DNS servers do not respond for any reason,
that distorts calculations of average values. The
exclusion of such abnormalities allows to calculate
more objective picture of the performance.
-
Display geo information - shows the flag of the
associated with the IP address territory. If the DNS record
contains multiple IPs in different territories, only the
first territory is shown.
-
Activity view filters

displays the filter bar at the top of the log window with checkboxes to filter different types of activity events.
These filters affect only the view and not the persistent
log.
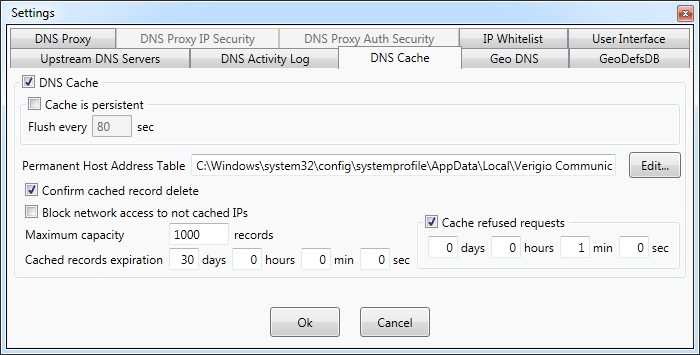
Settings - DNS cache
DNS Proxywall maintains it own DNS cache. All requests and responses are stored within that cache.
When request is resolved via cache rather than via remote DNS server, it saves time on
the round-trip packet travel.
The total number of cache requests and resolves per DNS server is displayed on Servers tab of the main
window.
By default, the cache is kept in memory and reset each time the DNS Proxywall service restarts.
The option Cache is persistent forces the cache to be saved on disk periodically and loaded upon DNS
Proxywall service start.
The cache contains records that come from other (upstream) servers. For hosts that have permanent IP addresses,
DNS Proxywall has PermanentHostAddressTable.hostaddr file
where permanent IP addresses for server names can be
specified. This file is used during IP address resolution before the cache
lookup and
before sending packets to remote (upstream) servers. Its functionality is similar to hosts file on Windows.
The format is similar to the hosts file as well.
Each line could be a blank
line, a comment line, or a line with an IP address specification.
[*.]domainname IPAddr1[,IPAddr, ...] [Category] [# comments]
Examples
-
The exact case-insensitive match for verigio.com
verigio.com 192.168.1.1 PermanentHostAddressCategory
The PermanentHostAddressCategory is a single word tag that describes the host.
-
Case-insensitive match to verigio.com and all subdomains
*.verigio.com 192.168.1.1,192.168.1.2 PermanentHostAddressCategory
The option Confirm cached record delete forces user interface
prompt for user confirmation when the user is attempting to manually delete record(s) from the cache.
DNS Proxywall supports the use-only-from-cache mode when only previously resolved and cached IP addresses
are used
while all other attempts to resolve new addresses are automatically rejected.
The use-only-from-cache mode is activated by Block network access to not cached IPs option.
Other cache parameters can be set as well.
-
Maximum capacity - maximum cache capacity beyond which the older records are replaced by the new ones.
-
Cached records expiration - force expiration of cached DNS records. This option helps to keep DNS records up-to-date.
-
Cache refused requests - whenever a request is rejected with the status
'no such server', the record can be cached so the subsequent requests to non-existent servers would fail faster.
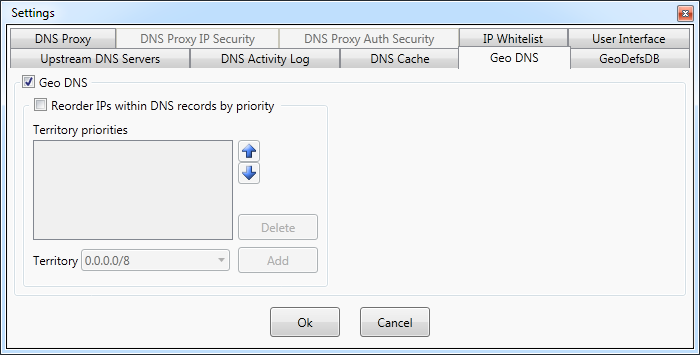
Settings - Geo DNS
Geo DNS allows to lookup the country of an IP address.
It also supports geographical prioritization which is reordering of IP addresses within each DNS record according
to specified priority list.
The IP addresses belonging to countries at the top of the list will be
used for connectivity first.
This improves connection performance when connectivity is with hosts located nearby rather than far away.
The geographical prioritization can be enabled with Reorder IPs within DNS records by priority.
The countries with higher priority should be placed at the top of the Territory priorities list. The
dropdown box contains all the territories and networks that can be
added to the priority list.
NOTE: it sometimes takes up to 1 minute to populate this dropdown box
at first.
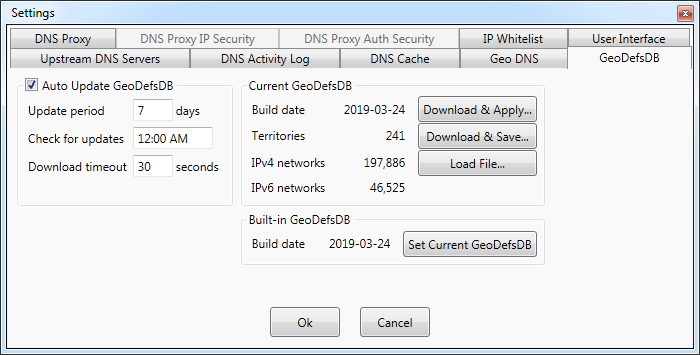
Geo Definitions Database (GeoDefsDB) update settings
Geo definitions (Geo IP) database contains mappings between geographical territories and IP addresses.
This database is stored in a proprietary format.
The program comes within the internal (embedded) Geo IP database that is
used in absence of later database versions. This embedded database can be
set as the primary(active) database by clicking Set Current GeoDefsDB
button. Updates to the Geo IP database can be downloaded
from our website using this settings page or they can be set
to download automatically at predefined time.
The initial time at which the download is performed is
generated randomly upon the first program start.
The database can be set to automatically download at the specific time of day with a period of several days.
The settings for auto download can be found under Auto update GeoDefsDB section.
Geo definitions can also be downloaded manually and saved into a file using Download and Save... button. This helps
to manually manage what geo definitions are used.
The loading of geo definitions database can be done with Load File... button.
Settings - DNS proxy
DNS Proxywall can act as a DNS server to other computers on the network.
The standard DNS server (proxy) functionality is enabled by Standard DNS proxy server setting. When this
functionality
is enabled, DNS Proxywall is listening for incoming DNS requests on
UDP port and sending responses either based on its own cache or based on responses from the upstream DNS servers.
The standard DNS server
(proxy) functionality supports the widest range of DNS clients from personal computers to mobile phones.
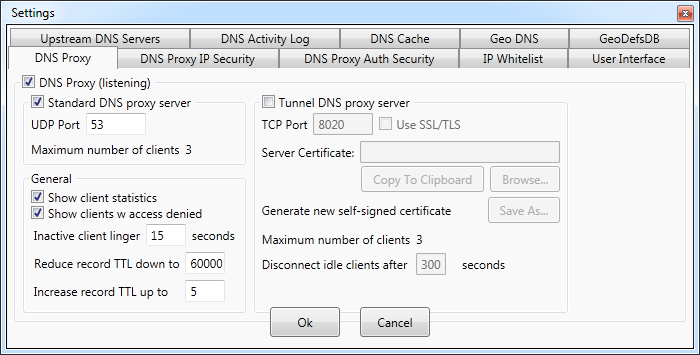
DNS Proxywall also supports tunneled communication. The tunneled communication is
a proprietary Verigio protocol and is supported only for traffic between DNS Proxywals.
This protocol packages all DNS traffic into a single TCP connection. This feature is commonly used for aggregation
of DNS traffic
for forwarding to a centralized server(s) via reliable TCP protocol.
The tunneled communication listener can be turned on with Tunnel DNS proxy server option.
TCP communication can also be encrypted with SSL/TLS protocol on top of the TCP.
When encryption is enabled with Use SSL/TLS, two sides to communication use certificates to encrypt the traffic.
Those certificates can be issued by a standard certification authority (CA) or self issued and self signed.
When two sides start communication with enabled SSL/TLS, they verify each other's certificates using the SHA-1
checksum. The client knows SHA-1 of the server certificate and the server knows SHA-1 of the client certificate. They both
verify SHA-1 of each other, and only then proceed
to establishing the connection.
TCP is a connection oriented protocol. Which means that a connection between
a server and a client exists until one of the sides decides to
disconnect.
To prevent multiple clients from consuming server's resource
by staying idle, Disconnect idle clients after option forces disconnect of such clients
after the specified timeout. When disconnected clients become active
again, they would re-connect to DNS Proxywall.
Settings - DNS proxy IP security
Placing a personal DNS proxy on the Internet could be quite risky without
the proper security.
DNS Proxywall supports verification of clients by IP addresses.
Only requests coming from the specified IP addresses and subnets
are processed by the program. Other requests are simply ignored.
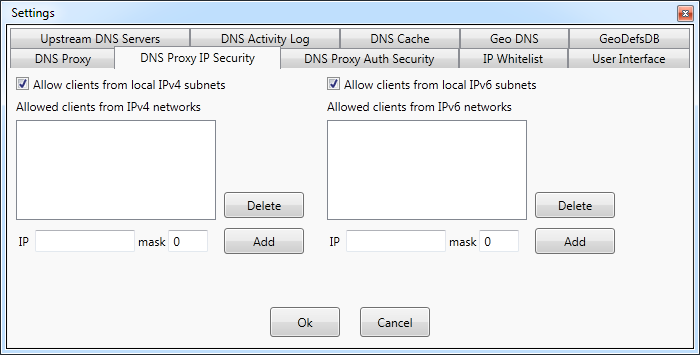
The options Allow clients from local IPv4 subnets and Allow clients from local IPv6 subnets automatically
add IP addresses of all computers on the local network to the list of allowed client IPs.
Whether IP is on local or not local network is determined by the network mask(s) configured by DHCP during connect
to the network.
Settings - DNS proxy Auth security
The next level in securing the DNS Proxywall in proxy mode is the
certificate authentication security.
This feature is supported only for tunnel based communication: DNS over TCP, or DNS over SSL/TLS.
It allows to ensure authentication of DNS clients with no regard for their IP addresses.
In other words, it works independently from IP security.
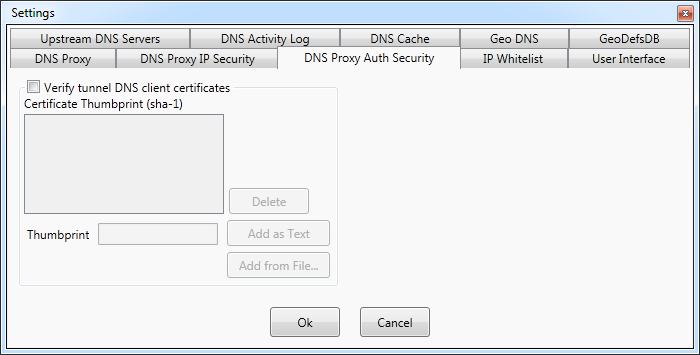
DNS Proxywall verifies SHA-1
(a.k.a. Thumbprint) hashes of digital certificates provided by clients. Only when certificates match the
connection is established.
Verification of client certificates is enabled via Verify tunnel DNS client certificates option.
The SHA-1 hashes of allowed certificates can be added to the list as hexadecimal text using Add as Text
or calculated from the exact client certificate file using Add from File.
Hexadecimal SHA-1 text of a certificate can be obtained using either a web browser or just by viewing the special
fields of a certificate.
The calculation of SHA-1 can be performed on *.p12 (Personal Information Exchange) files. Such files can be
encrypted with password as well.
Settings - IP Whitelist
DNS Proxywall rules can block
wide range of IP addresses via Geo DNS or via blocking of non-DNS IPs.
Sometimes, it is important to guarantee that communication with local
network and certain other IP addresses does not get blocked.
IP Whitelist allows to exclude IP addresses from such blocking. Whenever DNS Proxywall is managed in
the cloud via Remote Desktop, adding your own IP address
to the whitelist would prevent locking yourself out by accidental change in rules.
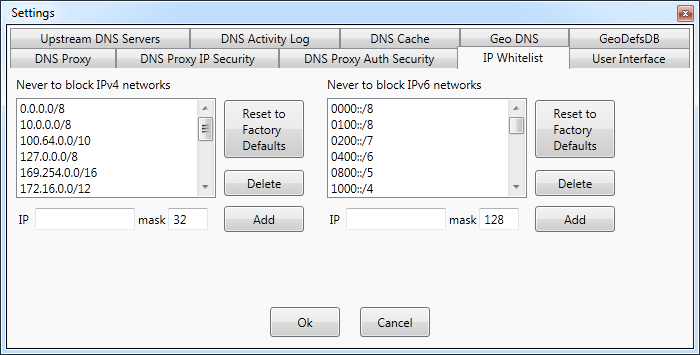
By default, whitelists contain IP addresses that are considered to be special addresses that rarely require any blocking.
Whenever changes to the whitelist is needed to be reverted, Reset to Factory Defaults would reset it each whitelist
to its original state.
Settings - User Interface
DNS Proxywall has a very dynamic graphical interface. Not all servers have high-end graphics cards that can draw so much
graphics efficiently.
Therefore, adjusting UI performance is one of the ways to improve overall system performance.
DNS Proxywall user interface is needed
only for management of the DNS Proxywall service. Once the settings are set, UI can be closed completely.
In cases when UI is needed to be on and the overall performance is needed as well, UI performance settings
panel allows to adjust various graphical features to better suit the needs.
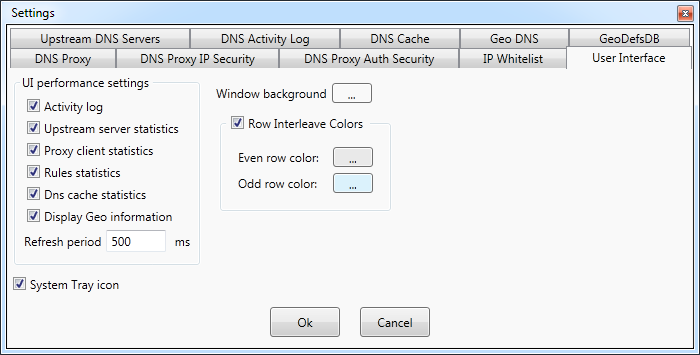
- Activity log - enables or disables activity logging. It is the equivalent of the setting on the DNS Activity Log
tab.
- Upstream server statistics - enables or disables calculation and display of statistics for upstream DNS servers.
It is the equivalent of Show server statistics option on the Upstream DNS Servers tab.
-
Proxy client statistics - enables or disables calculation and display of statistics for proxy clients. It is the
equivalent of Show client statistics option on the DNS Proxy tab.
- Rules statistics - enables or disables calculation and display of statistics for name pattern rules.
- DNS cache statistics - enables or disables calculation and display of statistics for each DNS cache record.
- Display Geo information - enables or disables displaying of country flags next to IP addresses.
- Refresh period - refresh period for all statistics. The smaller it is the more overhead it results in.
System tray icon -- allows user interface upon close to be minimized
instead to the system tray area of the task bar.
Notes:
* Windows® is a registered trademark of the Microsoft Corporation.